IN THIS ARTICLE
Best WordPress security plugins: Why a layered defense is key
When searching for the best WordPress security plugins, it’s easy to get dazzled by plug-and-play solutions that promise “one-click” protection. After all, WordPress runs over 40% of the web, so the need for reliable security is obvious. Yet, there’s no magic bullet. True security requires multiple lines of defense, each tailored to protect different vulnerabilities.
In this guide, we’ll unpack the layers of WordPress security, then highlight the limitations of single, all-in-one solutions. From there, we’ll explore specific single-use plugins and best practices—like regular updates—to safeguard your site properly.
Understanding the layers of WordPress security
Think of your WordPress site as a tall, multi-layer cake. Each tier has its own flavor and texture, and if you neglect even one layer, the entire dessert suffers. The same idea applies to security: every layer—server-level protections, edge-level defenses, application safeguards, and user oversight—contributes to a fully secured “cake.” You wouldn’t rely on just a fancy icing or topping to protect the whole thing. Effective security takes a layered approach, typically spanning:
- Server-Level Security – The cake foundation
- Application-Level Security – The delicious cake filling
- Edge-Level Security – The frosting
- User-Level Security – The decorations
Server-level security

Think of server-level security as your cake stand—the sturdy foundation that holds up everything else. Even the fluffiest frosting (your firewall) can’t compensate for a wobbly base. By investing in a proper managed host and ensuring solid server configurations, you’re making sure the entire cake stands firm, layer upon layer. Here’s what to consider for your security foundation:
- Hosting environment: Your hosting environment sets the tone for your entire site, so it’s wise to choose a cutting-edge managed WordPress host—like WP Engine, Kinsta, or Pagely—that invests in dependable server setups and modern PHP versions. If you’re just dipping your toes into WordPress, a shared hosting account might suffice. But upgrading to a dedicated or high-end managed hosting plan gives you a bigger say in security matters, reducing the odds of sneaky vulnerabilities slipping through the cracks.
- Malware scanning: Some hosts and other third-party services like Sucuri and Malcare scan continuously at the server level for malicious files. If malware scanning were implemented at the application level, it could easily be disabled by a WordPress user, leaving your site open to vulnerabilities.
- Secure database credentials: Your WordPress database is the beating heart of your site. If intruders get hold of it, they can tamper with your content, swipe user data, or even take over your entire website. To keep this door locked, always use a strong, random username and password—never something predictable like “root” or “admin.” For extra camouflage against automated attacks, swap out the default “wp_” table prefix for something unique (as long as your host supports it). Check out this guide from Kinsta for a step-by-step walkthrough.
Application-level security

If the server is your base layer and edge-level tools form the protective icing, then application-level security is the luscious filling of your WordPress cake. Themes, plugins, and core settings live here—and even if your foundation is solid, a flaw in these middle layers can spoil the entire dessert. That’s why specialized scanning, login safeguards, and frequent updates matter so much.
- Core WordPress: Regular updates to the WordPress core often contain crucial security fixes. If you ignore these updates, you’re leaving the door wide open for attackers who know how to exploit unpatched software. Keeping WordPress current also boosts site stability and includes performance improvements.
- Themes & plugins: Every theme and plugin is a potential vulnerability if the code is outdated or poorly maintained. Hackers routinely scan for known flaws in popular add-ons, hoping to gain backdoor access. By updating themes and plugins regularly—and removing any you no longer use—you close those loopholes and maintain a more secure, reliable site.
- Activity monitoring & vulnerability scanning: Specialized tools in this category keep a watchful eye on your site’s files, user actions, and database. They’ll detect suspicious code snippets or patterns (like known malware signatures) and send alerts right away. This proactive defense helps you contain an attack before it spreads or inflicts major damage.
- Login protection: Brute-force attacks—where bots test endless username/password combinations—are a constant threat. Limiting login attempts, using strong passwords, or enabling multi-factor authentication can drastically reduce unauthorized access. This extra guardrail ensures that even if someone stumbles upon your credentials, they’ll still need another layer of verification.
Edge-level security

If the server layer is the base of your cake, then edge-level protection is like the sweet coating around the outside—keeping germs, dust, and sticky fingers at bay before they can mess with the layers beneath. Services like a Web Application Firewall (WAF) or a CDN act as that protective icing, filtering suspicious traffic and thwarting DDoS attacks so your WordPress “cake” stays pristine inside. Here’s are some techniques available to you to protect the edge:
- Web Application Firewall (WAF): A WAF intercepts malicious traffic—such as DDoS or injection attempts—before it ever reaches your hosting server. By deploying specialized rulesets for common WordPress exploits, a service like Sucuri or Cloudflare can filter out sketchy requests at the edge. This prevents attackers from even seeing your login page or database, dramatically reducing your exposure.
- Bot management services: Instead of using a traditional WAF, you can opt for a dedicated bot management solution that weeds out harmful or suspicious bots at the perimeter. By distinguishing human visitors from automated threats, these services help keep your site’s performance intact and stop malicious scrapers or brute-force attempts before they gain traction. Cloudflare also has a number of bot management tools built into its Pro tier, which is included for every SiteCare Gold (or above) client.
- Security Headers: Implementing features like HSTS (HTTP Strict Transport Security) and disabling older TLS versions at the edge ensures all traffic between your site and visitors is encrypted and up-to-date. This setup protects against eavesdropping, downgrade attacks, and other man-in-the-middle threats, making it much harder for hackers to snoop or tamper with your data as it moves across the web. If you’re curious about HSTS implementation to protect your site, get in touch.
User-level security

If the base layer is strong, the icing pristine, and the filling scrumptious, then user-level security is the fancy piping or ornate toppers on your WordPress cake. Even a perfectly baked cake can be ruined if someone carelessly pokes their fingers into it—so think of strong passwords, limited privileges, and two-factor authentication as the decorative swirls that keep every last crumb safe and beautiful.
- Strong Passwords: Reusing the same old password makes it easy for bad actors to crack your account. Complex, random passwords—or those generated by a trusted password manager—are much harder to guess or brute-force. Requiring users to regularly update their credentials lowers the chance of someone sneaking in.
- Role Management: Handing out admin rights to everyone is like giving all your houseguests the key to your safe. Limit each user to only the permissions they need. The fewer people who can install plugins or change theme files, the lower your risk of accidental damage or deliberate tampering.
- Two-Factor Authentication: A stolen password on its own shouldn’t be enough to break in. Two-factor authentication adds a second checkpoint—like a text message or authenticator app (our recommended configuration)—so even if an attacker has your password, they still need the unique code to proceed. This extra hoop drastically reduces the chance of unauthorized logins.
- Activity Logs: If something fishy happens—like an unexpected plugin installation or a mysterious settings change—activity logs help you pinpoint who did it and when. Having a running history of actions on your site allows you to investigate quickly, fix issues, and avoid repeat incidents.
Where kitchen sink plugins fall short
Now that we’ve seen how many layers go into WordPress security, we can address why relying on a single “kitchen sink” plugin is often a bad idea.
Single point of failure
A monolithic security plugin might claim to handle malware scanning, brute-force protection, and more. But if that plugin has a critical vulnerability, a compatibility issue, or gets disabled, all your defenses can crumble at once.
Incomplete coverage
Many one-click solutions focus primarily on application-level security. But even the best WordPress security plugins can’t replace robust server configurations or edge-level WAF services. Plus, none of the popular all-in-one plugins can enforce strong user passwords or usage policies without user cooperation.
Resource hogging & bloat
All-in-one security tools can become bloated, scanning everything under the sun and hogging CPU or memory. You might end up with features you don’t need—or worse, modules that conflict with other plugins, causing slow performance or site errors.
In short: No single plugin can secure every aspect of your site. A layered approach (plus some specialized plugins) is far more effective.
The best WordPress security plugins for specific tasks
Below, you’ll find a curated list of specialized plugins. Each one tackles a distinct aspect of WordPress security, making them complementary building blocks in a layered strategy.
Patchstack: Vulnerability scanning and virtual patching
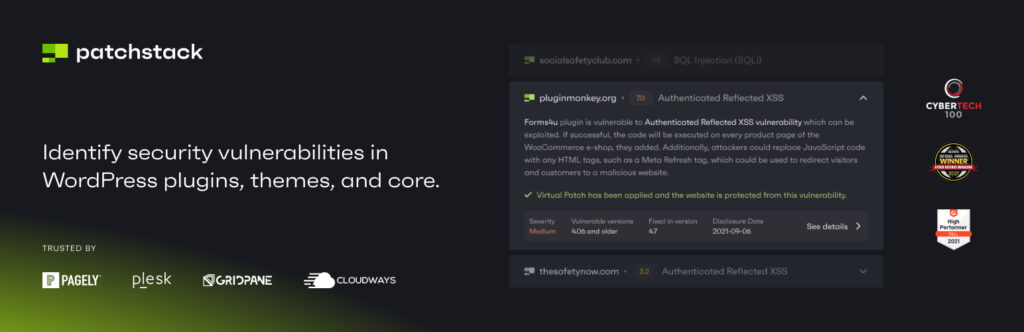
We recommend Patchstack because it keeps a vigilant eye on potential vulnerabilities in your WordPress site, especially for plugins and themes. Patchstack’s real-time scanning and “virtual patching” feature help protect you from newly discovered security flaws—sometimes before a developer can release an official fix. This proactive defense gives you peace of mind, knowing that if a known exploit emerges, Patchstack will be there to shield your site until a permanent patch is available.
- Core benefit: Patchstack continuously checks your site for known security issues in plugins and themes and WordPress core.
- Virtual patching: If a plugin is vulnerable but not yet patched by the developer, Patchstack can act as a temporary shield.
- Alerts and dashboard: You receive quick notifications when a threat is detected, and you can oversee multiple sites from one central interface.
Two-Factor (by Core WP contributors): Multi-factor authentication
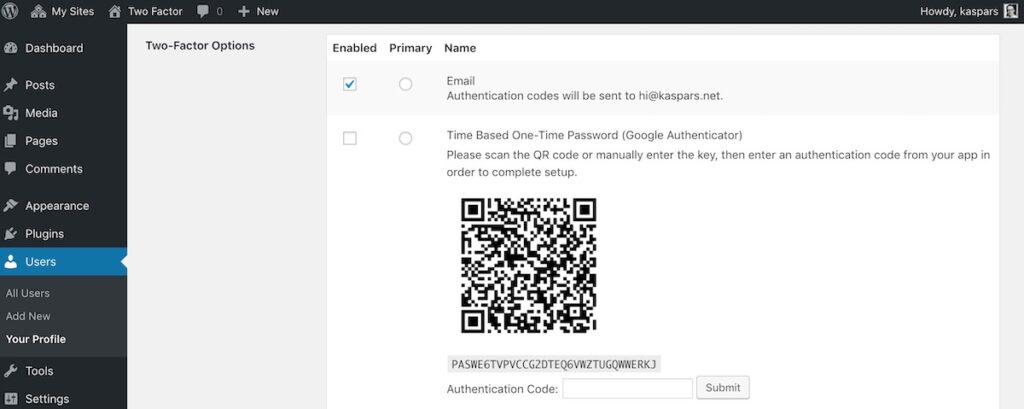
We recommend the Two-Factor plugin because it adds a second checkpoint to your login process—beyond just a password. Even if an attacker somehow learns your password, they can’t get in without that extra authentication step. Maintained by WordPress core contributors, the Two-Factor plugin integrates smoothly with the WordPress login system, so you gain powerful protection without sacrificing usability. We also have a useful guide for setting up Two-Factor with 1Password.
- Core benefit: Provides secure multi-factor authentication for WordPress logins.
- Minimal overhead: Doesn’t bog you down with extra features; it focuses on making 2FA easy to implement.
- Officially recognized: Maintained by contributors to WordPress core, ensuring solid compatibility and future-proofing.
Simple history: Tracking user activity
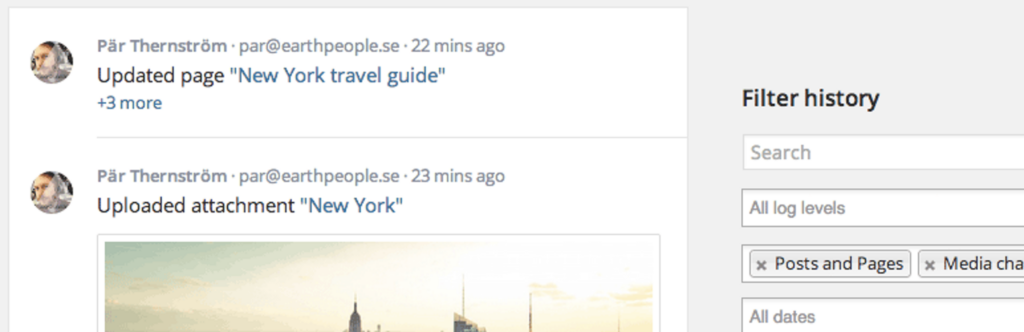
We recommend Simple History because it keeps a clear record of who changed what on your WordPress site. If someone installs a new plugin or adjusts vital settings, you can see exactly when it happened and who was responsible. This continuous activity log helps you quickly spot suspicious behavior or pinpoint the culprit if something goes wrong—perfect for maintaining accountability and peace of mind.
- Core benefit: Logs changes like plugin installs, updates, and post edits in a chronological timeline.
- Low impact: Lightweight, so it won’t significantly slow your admin area.
- Quick forensics: Makes it easy to identify who changed what if something goes wrong or looks suspicious.
Limit Login Attempts Reloaded: Brute-force defense
We recommend Limit Login Attempts Reloaded because brute-force attacks—where bots endlessly guess your password—are one of the most common threats to WordPress sites. This plugin thwarts those attacks by temporarily blocking IPs after a set number of failed attempts. By putting a strict limit on login tries, you make it significantly harder for automated intruders to break in, boosting your overall site security with minimal fuss.
- Core benefit: Blocks IP addresses after a set number of failed login attempts.
- Customized lockout settings: You decide how many tries to allow and how long to lock out repeat offenders.
- User-friendly notifications: Provides alerts when an IP is locked out, so you’ll know if your site is under brute-force attack.
Off-site backup services
We recommend using an off-site backup service because it protects your website data in a separate, secure environment—beyond the reach of potential hacks or server crashes. By storing backups outside your main hosting account, you can quickly restore a clean version of your site if anything goes wrong. This extra layer of insurance not only offers peace of mind but also saves countless hours of stress if disaster ever strikes.
Read our comparison of the Best WordPress Backup plugins.
- Core benefit: If your site is compromised, having a recent backup stored safely off your main server can be a lifesaver.
- Incremental and automated: Look for incremental backups (only changed data is backed up) and schedules to minimize resource usage.
- Easy restoration: One-click or guided restores, plus staging environments to test before pushing changes live.
General best practices for a secure WordPress site
Beyond plugins, effective security demands a bit of know-how. Here are some of the tactics we implement when onboarding a new client to a WordPress Maintenance Plans:
- Use SSL/TLS everywhere: Install an SSL certificate so your site always runs on HTTPS, and consider HSTS to ensure browsers only communicate securely. Enforce HSTS to force secure data transmission.
- Disable file editing: Disabling file editing ensures that even logged-in users can’t modify the code of your website directly. This prevents direct theme/plugin file edits if an attacker gains access.
- Secure your wp-config.php file: Restrict permissions (e.g.,
400or440) to limit who can read or change your WordPress configuration file. Some hosts even allow you to move it above the public HTML directory. - Enforce strong user roles: Assign roles carefully. For instance, most users don’t need the
administratororeditorprivilege—limit them toauthorif that’s all they need. - Don’t collect unnecessary data: The less user information you store, the less you have to lose in a breach. Follow data minimization principles to reduce potential targets for your website.
- Monitor activity regularly: Even with logs enabled, you have to review them or set alerts to catch anomalies early.
Keep themes, plugins, and WordPress core up to date
This point can’t be stressed enough: every update you ignore can be an open invitation to attackers.
- Plugin & theme updates: Most security vulnerabilities in WordPress arise from outdated or poorly maintained plugins/themes.
- WordPress core: Turn on auto-updates for minor versions at least, which often include critical fixes.
- Check changelogs: When a plugin update mentions “security fixes,” apply it right away.
No WordPress security plugin manages updates for you
Some plugins notify you about outdated components, but they don’t automatically perform updates—nor should they. Ignorantly auto-updating everything can break your site if there’s a conflict. It’s safer to handle updates methodically:
- Establish a baseline: Have clear documentation about the intended behavior and functionality of each component of your website.
- Test on a staging site: If possible, use a staging environment to check for compatibility.
- Incremental updates: Update one plugin at a time, testing your site after each.
- Keep backups handy: Always have a recent backup before performing a batch of updates.
A great security plan includes consistent attention to updates. No plugin can do that important human review for you.
Conclusion: Layer your defenses, then stay vigilant
While it’s tempting to install an all-in-one plugin labeled “best WordPress security plugin” and call it a day, genuine protection goes far beyond ticking a few checkboxes. By implementing security at multiple layers server, application, edge, and user levels you create a comprehensive shield that’s far tougher for attackers to penetrate.
With a layered defense and ongoing maintenance, your site stands a much better chance of repelling intruders and running smoothly for the long haul. No single plugin promises bulletproof security, but a thoughtful selection of the best WordPress security plugins combined with proper upkeep will get you as close as possible to a worry-free WordPress experience. For hands-on support and expert maintenance, consider working with WordPress SiteCare, where proactive monitoring and layered security practices are built into every plan.




Leave a Reply