IN THIS ARTICLE
We uncovered the hacked WordPress site during our onboarding process, and the client had no idea their site had been compromised, let alone completely pwned—meaning it was fully controlled and exploited by an attacker. What made things even worse — it was a membership website, meaning user data and activity were at risk. The situation required our immediate attention to regain control. Nearly 2,000 files were infected, multiple database tables were corrupted, the client was on the precipice of losing user trust. Their digital storefront—critical to their business—was effectively a playground for cybercriminals.
We found malware embedded in plugins, core files compromised, and rogue PHP scripts lying in wait for their next malicious move. This wasn’t a run-of-the-mill cleanup—it was a total rehabilitation.
Let’s break down how our team at SiteCare tackled this digital disaster and restored their site to health.
A snapshot of the damage: When malware runs amok
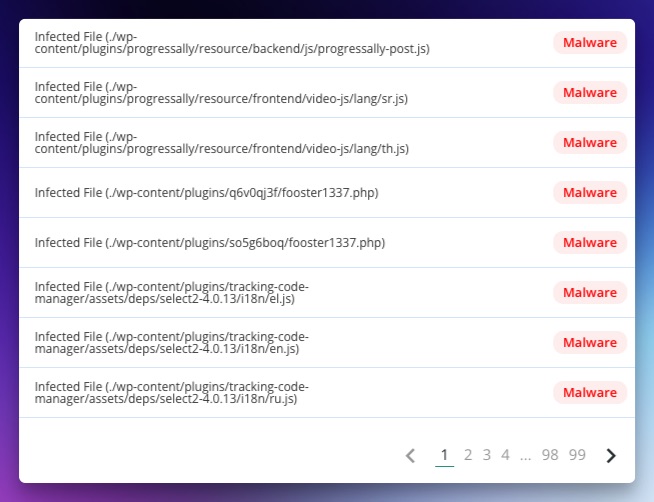
From the moment we accessed the compromised environment, we could see the infection was widespread. Our security tool flagged 1,970 malicious files and one rogue script, many of which were in critical plugin directories like:
- ProgressAlly: Malicious JavaScript files like
progressally-post.jswere injected to exploit front-end functionality. - Tracking Code Manager: Hackers exploited i18n assets (e.g.,
select2-4.0.13/i18n/en.js) to distribute phishing links disguised as language support files. - Custom PHP backdoors: Files such as
fooster1337.phpin plugin directories acted as “backdoor scripts,” allowing attackers to regain access even after initial cleanup.
In cases like this, hackers often use obfuscation techniques to conceal malicious payloads within legitimate-looking files. These scripts can include a variety of base64-encoded strings, randomized function names, and chained operations to hide their true intent. All of these are digital trojan horses. On the surface everything looks copacetic, but deep within the code there are serious threats that can be difficult to detect.
Beyond the files, the database was infiltrated. One table was completely compromised with injected spam links and redirects targeting unsuspecting users. This isn’t just an annoyance—it’s an SEO nightmare. Google flags infected sites, meaning the client’s traffic and reputation were both circling the drain.
How we took back control of the hacked WordPress site: A multi-layered approach

If you’re looking for how-to steps for cleaning malware from a hacked WordPress site, I recommend checking out Malcare’s guide for cleaning a malware infection. To see how our team tackled this particularly messy infection, read on.
1. Immediate containment
First, we quarantined the infected environment. By temporarily taking the site offline, we halted malicious activity and ensured the infection wouldn’t spread further. This step is crucial in limiting the scope of damage, particularly for membership sites where user data and transaction and usage activity are at risk.
We also reset all access credentials—including admin accounts, SFTP, and database connections—to lock out unauthorized access. Hackers often create hidden admin accounts to maintain control after a breach, so a thorough audit of user roles was essential.
2. File-level malware cleanup for a hacked WordPress site
Cleaning nearly 2,000 infected files required a combination of automated and manual techniques:
- Automation with precision: We used malware scanners to identify files with known malicious signatures. Tools can quickly flag patterns, but they’re not perfect. For example, they can’t reliably detect obfuscated scripts that resemble legitimate code.
- Manual code review: Our team went line by line through critical files—especially in
/wp-content/plugins/and the client’s themes. For instance, we found and removed suspicious base64-encoded payloads, often embedded within JavaScript and PHP files. Example:eval(base64_decode('aWYoIWZ1bmN0aW9uX2V4aXN0cygnaGVsbG8nKSl7ZXZhbCg...'));This is a classic hacker trick: encoding malicious functions to avoid detection. - File restoration: Where possible, we replaced infected files with clean copies from the WordPress repository or official plugin directories. In some cases, we patched custom code instead of overwriting it to preserve functionality.
3. Database repair
The database presented a unique challenge. Infections at this level typically involve SQL injection attacks where hackers insert malicious scripts into tables. In this case:
- The posts table contained spammy redirects embedded in post content, targeting external phishing domains.
- Metadata tables included injected payloads designed to execute silently during routine operations.
To clean the database:
Analyzed backup snapshots: We compared the current database against backups to identify discrepancies. This helped us pinpoint the injected data and restore tables to their original state.
Sanitized input fields: For example, any field accepting user input (e.g., comments, custom forms) was scrubbed to remove embedded scripts.
Hardened database permissions: We limited write access to critical tables and enforced stronger user authentication for database connections.
4. Strengthening security
Once the malware was eradicated, we shifted our focus to hardening the site. This included:
- Implementing a Web Application Firewall (WAF): The client’s site now filters malicious traffic before it even reaches the server.
- Configuring real-time monitoring: Using a security stack that includes server-level logging, file change detection, and proactive alerts.
- Regular backup schedules: Incremental backups ensure we can restore the site quickly in case of future issues.
- Disabling dangerous PHP functions: Functions like
eval()andexec()—often used in backdoors—were disabled at the server level.
Uncovering hidden costs: How malware impacts more than just security and reputation
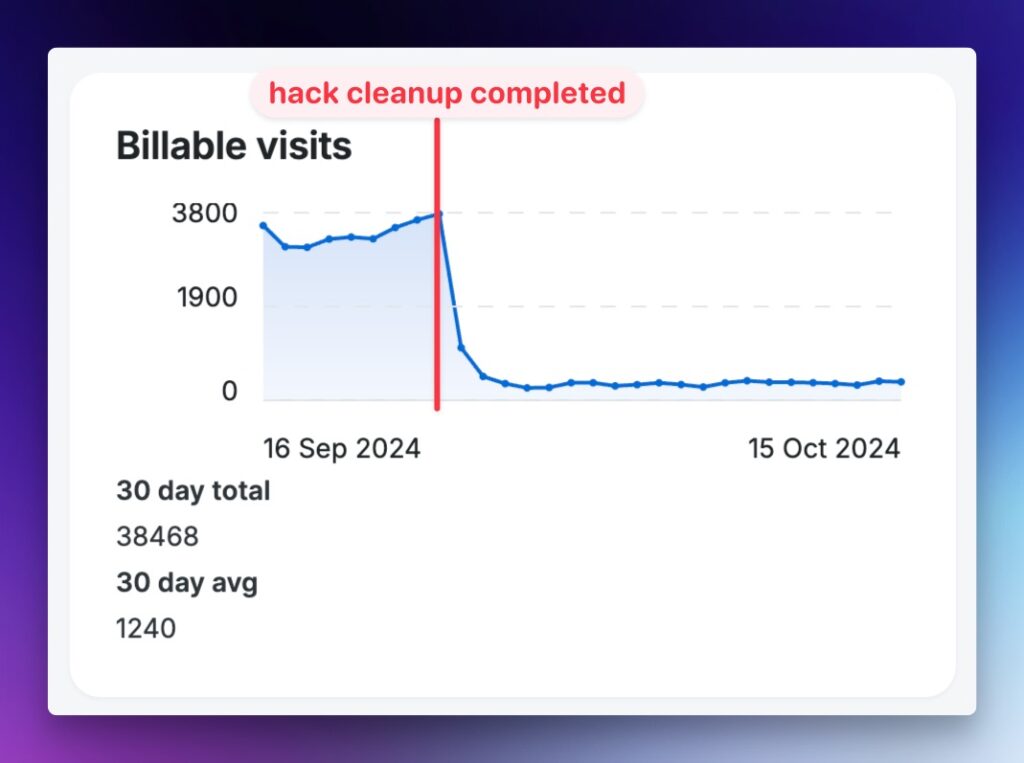
As we worked through the hacked site’s cleanup, another unexpected consequence of the hack came to light: the malware wasn’t just sabotaging the website’s functionality; it was also inflating the client’s hosting costs. Malicious scripts and spam traffic were artificially driving up the number of billable visits to their hosting account.
For context, this client was using WP Engine, a hosting provider that calculates monthly costs based on site traffic. With thousands of fake visitors being funneled through the site by the malware, their billable visits soared far above normal levels. After removing the malicious code and cleaning up the database, the client’s traffic metrics normalized, resulting in significant savings on their hosting bills.
This was an eye-opener—not just for the client but for anyone running a website. Malware isn’t just a technical problem; it can quietly drain your budget in ways you wouldn’t expect. By restoring their site and addressing the root cause of the inflated visits, we didn’t just clean their site; we helped protect their bottom line.
Lessons for website owners: Why WordPress gets hacked and how to prevent it
The vulnerabilities that led to this hack weren’t unique. Most infections happen due to common oversights like outdated plugins, weak passwords, or improper file permissions. In this case:
- Outdated WordPress core: The client was running version 6.6.1, which had known security vulnerabilities.
- Inactive outdated plugins: Hackers exploited dormant, outdated plugins to gain entry. Remember, even inactive plugins can pose risks if they’re outdated or poorly coded.
This experience highlights why ongoing maintenance is critical. A secure website isn’t a “set it and forget it” deal—it’s an ongoing process of monitoring, updating, and securing.
Protecting your reputation and revenue
When a site gets hacked, the financial and reputational fallout can be catastrophic. Beyond the immediate cleanup, the client faced:
- Loss of trust: Users will become very reluctant to interact with a flagged site.
- Decreased search rankings: Google penalizes hacked sites, pushing them down in search results.
- Potential legal risks: Depending on the region, failing to secure user data can result in fines.
By stepping in, we not only cleaned their site but also restored their ability to operate confidently. And that’s what we’re here for—to be the safety net when things go wrong. Or better yet, to keep things from going wrong in the first place.
Final thoughts: Your partner in website security
This story has a happy ending, but not every hacked site is so lucky. The key takeaway? Prevention beats remediation every time. By investing in professional maintenance and security, you can avoid the stress, downtime, and expense of a major hack.
If you’re wondering how secure your site is—or if you’re dealing with a similar crisis—reach out to us. At SiteCare, we bring the expertise, tools, and determination to tackle even the toughest malware infections.
We take trust and security seriously, achieving certification in Enterprise WordPress Security by WordPress VIP. Get in touch today to learn how we can keep your WordPress site safe.



Leave a Reply